Equinix Data Center Giant Hit by Netwalker Ransomware, $4.5M Ransom
Ransomware attackers are demanding $4.5 million from Equinox
read morePublished on: May 19th, 2017

Posted: May 19, 2017 by Adam Kujawa
We just wanted to shoot out a quick blog post to let you know about a decryptor (Wanakiwi) that has been developed for WannaCry/WannaCrypt/wCrypt. There is a catch though, it only works for the following operating systems:
Windows XP
Windows Server 2003
Windows Vista
Windows Server 2008
Windows Server 2008 R2
Windows 7
So if you’ve got a WannaCry infection on one of the above operating systems, there is hope!
IMPORTANT:
The decryptor is only going to work if you haven’t restarted the infected system and you haven’t killed the ransomware process (should be wnry.exe or wcry.exe) so please don’t restart or kill the process if you want to get those files back!
Usage
In order to use this tool, you first need to download it from here.
This tool essentially searches the system’s memory for prime numbers and pieces together the encryption key used. However, it relies on current running memory so once you reboot it will be gone and if you’ve done too much on the system since infection, it’s possible the key won’t be found (because it’s been overwritten by data from other applications using the same memory space).
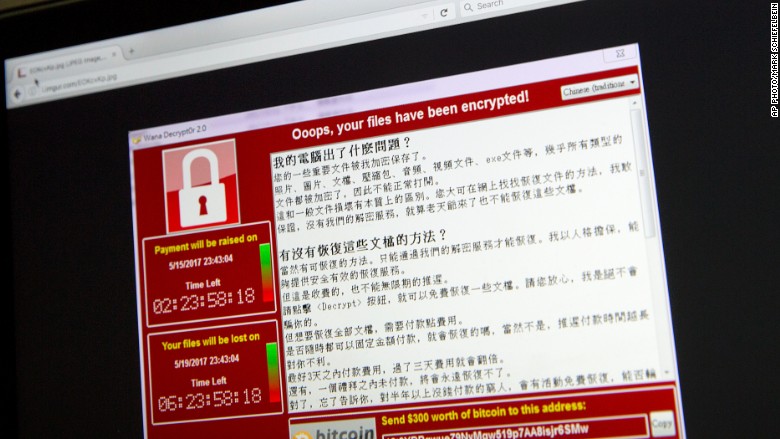
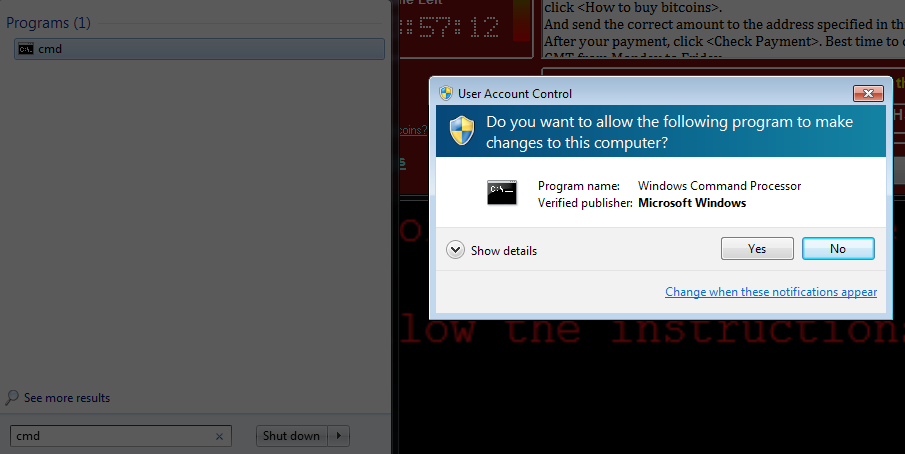
To run it, download the linked file (above) and extract the .zip to a folder on your desktop, (if you can download the file from a clean system and then transfer it via USB, you run less risk of overwriting the key in memory).
Next, you can either double click it (boring) or open the command prompt (Start + CMD) and run it through there (fun!).
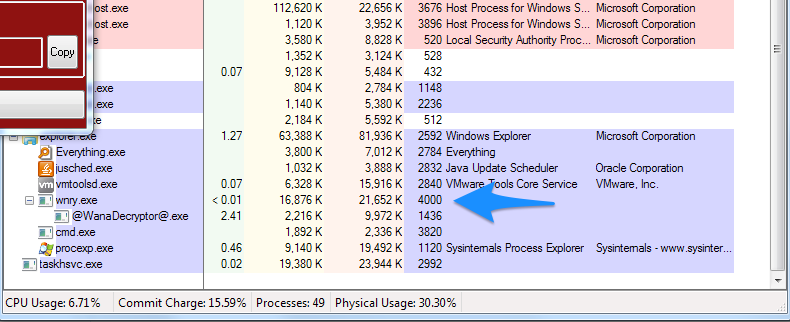
The tool will automatically identify the WannaCrypt applications running on the system if they are called wnry.exe or wcry.exe, but if for some reason they can’t find them, maybe check out the running applications on your system (Task Manager/Process Explorer) and find the offender (it’s pretty obvious), then identify the Process Identification Number (PID) and you can just plug that into the command prompt after wanakiwi.exe.
It might take a few minutes for the tool to find the key (or many minutes in some cases), but once it’s found the tool is going to start searching your system for encrypted files and decrypt them automatically.
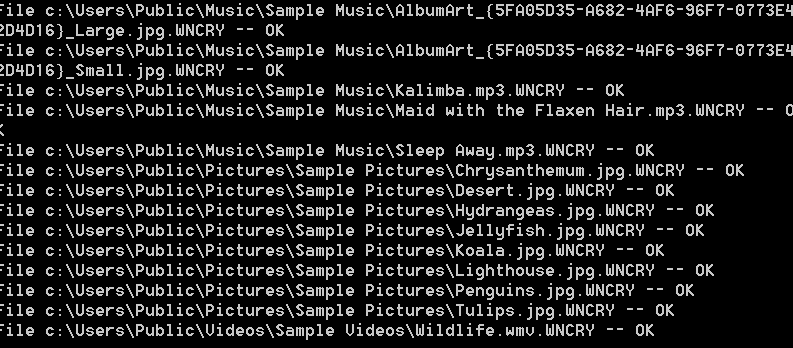
After the tool finishes decrypting your files, you are going to be left with a ransom note as a background and lots of encrypted files next to your unencrypted files.
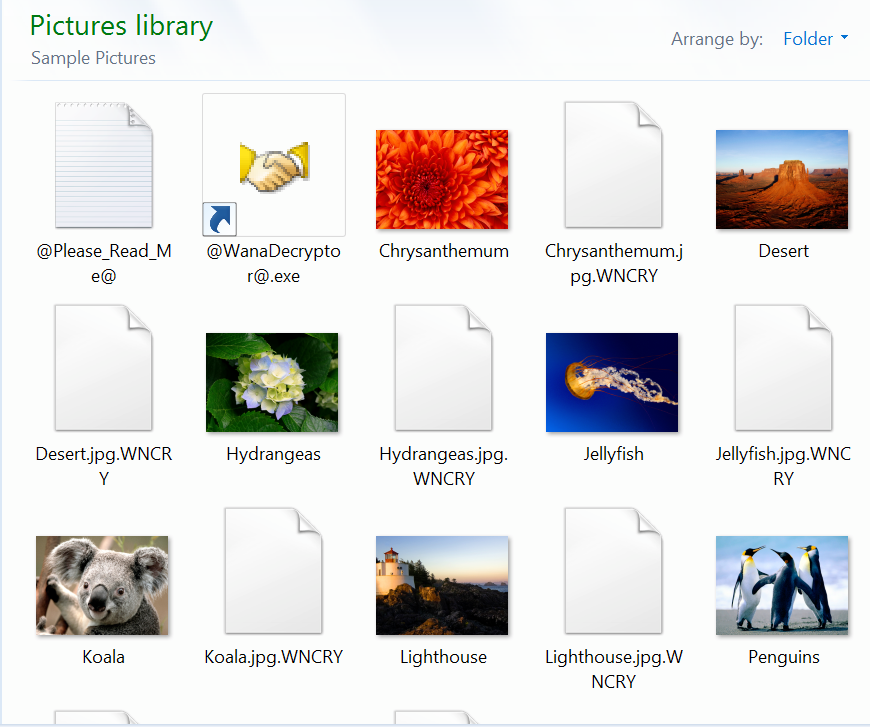
Here are some possible next steps:
Download Malwarebytes 3.0 (or whatever scanning tool you prefer that can clean up WannaCry) and run a scan on the system to identify all artifacts related to WannaCry. This will help you get the malware off the system in case it tries to encrypt again.
Restart the computer to finish clean-up.
Find all the most important files you want to keep and move them to some form of backup.
Wipe the system and reinstall Windows.
OR you can just go through your system looking for all files with the .WNCRY extension and getting rid of them.
Background
The original memory scrubbing, prime number searching WannaKey decryptor tool (for XP) was written by Adrien Guinet (@adriengnt) and then used as the base for Wanakiwi developed by Benjamin Delpy (@gentilkiwi). These guys are incredibly talented and deserve a round of applause!
We found out about the tool thanks to the very extensive blog post by Matt Suiche (@msuiche), which you should check out to get more information about how these tools work. You might remember Matt from his assistance in stopping a variant of the WannaCry released last week by registering the killswitch domain.
Effectiveness
We didn’t want to write about this tool until we tested it in some capacity. A lot of other security researchers have given it a go and it seems that the tool works well in lab environments (sometimes). I personally tested it on a Windows 7 system using the following sample (with mixed results):
ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
My first test worked like a charm.
My second test with a new profile (for taking screenshots for this post) couldn’t actually launch the malware.
My third test launched the malware, but the decryptor took forever and eventually never found the key.
My fourth test worked like a charm again (original profile).
Some of our other researchers tried it and were unable to get the tool to find the key.
Conclusion
This tool was put together very quickly and it’s meant to help those that it can help and that is likely not everybody. I wouldn’t recommend putting all your eggs in the basket that if you get hit, you couldn’t decrypt using this tool because either:
You are likely going to be unable to recover the key OR
The malware will modify to clean up the running memory or force a reboot after install to make the tool ineffective
But if you are currently dealing with a WannaCry infection, you have barely touched the infected system(s), and you are running one of the operating systems listed at the beginning of this post, running the tool is not going to break anything that isn’t already broken so it’s worth a shot just to see if you can get those files back.
That being said, once again big thanks to @adriengnt, @gentilkiwi & @msuiche for their hard work, information spreading and ingenious development skills.
Let us know in the comments if this tool worked for you (and your configuration too!)
With an evolving business comes expanding technological needs. If your business is sending you any of these signs that it’s time to update your technology.
Ransomware attackers are demanding $4.5 million from Equinox
read moreCybersecurity executives claim working from home increases the risk of attacks.
read more© 2024 Computer Troubleshooters. Privacy Policy