The SamSam ransomware has earned its creator(s) more than $5.9 million in ransom payments since late 2015, according to the most comprehensive report ever published on SamSam’s activity, containing information since the ransomware’s launch in late 2015 and up to attacks that have happened earlier this month.
Compiled by UK cyber-security firm Sophos, the 47-page report is a result of researchers collecting data from past attacks, talking to victims, and data-mining public and private sources for SamSam samples that might have slipped through the cracks.
In addition, Sophos researchers also partnered with blockchain & cryptocurrency monitoring firm Neutrino to track down transfers and relations between the different Bitcoin addresses the SamSam crew has used until now.
233 SamSam victims paid the ransom
By tracking all the Bitcoin addresses researchers were able to find, Sophos says it identified at least 233 victims who paid a ransom to the SamSam crew, of which, 86 went public with the fact that they paid the ransom, allowing Sophos to create profiles about each of these victims.
Researchers say that based on the data of these 86 victims, they were able to determine that around three-quarters of those who paid were located in the US, with some scattered victims located in the UK, Belgium, and Canada.
Half of the victims who paid were private sector companies, while around a quarter were healthcare orgs, followed by 13% of victims being government agencies, and around 11% being institutions in the education sector.
The Sophos team says it identified 157 Bitcoin addresses used in SamSam ransom notes that received payments, and another 88 who did not receive any money.
The total funds stored in these addresses is around $5.9 million, which is way more than previous estimates about the group’s financial prowess that had its earnings at only $850,000.
Sophos says that SamSam usually makes around one victim per day, and one in four victims pay the ransom.
“After the victim pays a ransom, the attacker will almost always transfer the money to multiple different accounts on the same day. On many occasions where the victim has paid half the ransom, the attacker will wait until the second half has been paid before transferring the full amount,” the report reads.
The most the group earned from one ransom alone is $64,000, according to Sophos, which is way more than your typical ransom payment that ranges between $200 and $1,000.
SamSam has remained largely the same
The reason for this huge ransom payment is because of the way the SamSam group operates. SamSam has always been different from most ransomware threats since the moment it first appeared in late 2015.
Its creators never used mass-distribution tactics such as email spam, exploit kits (malvertising), or fake update sites/software. Instead, the SamSam crew targeted one victim at a time. Initially, they used a known vulnerability in JBoss servers to target companies with Internet-accessible and unpatched JBoss installs.
As JBoss owners patched their servers and it became harder to find new victims, the group moved to searching the Internet for networks with exposed RDP connections, and mounting brute-force attacks against exposed endpoints, in the hopes of finding at least one machine that used weak credentials.
Once inside a network, the SamSam crew would spend as much time as it could scanning the network, mapping its layout, and using various legitimate tools such as PsExec to expand their access to local servers from where they could infect other workstations.
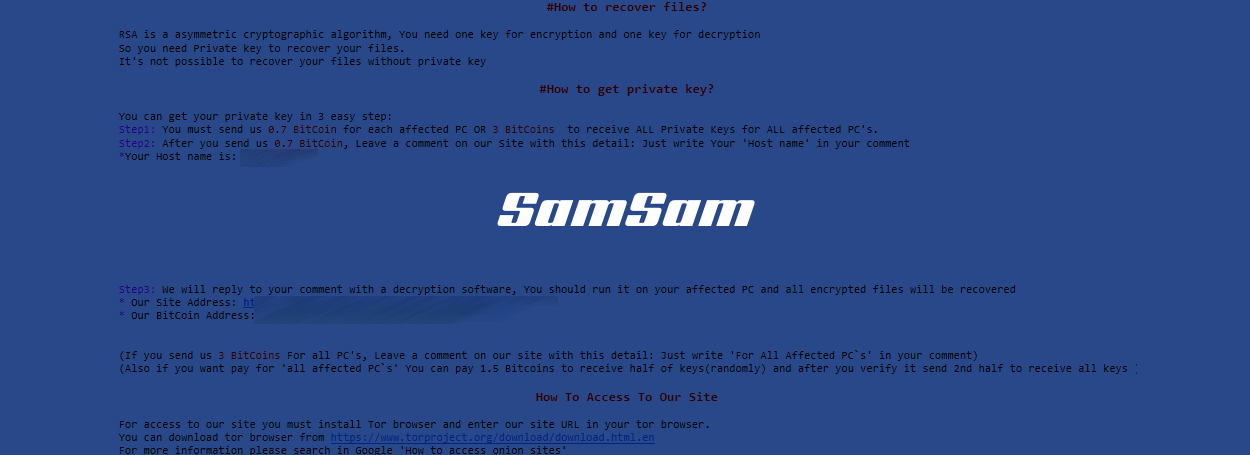
Once they had the access they needed, SamSam operators would wait until the weekend or nighttime to manually deploy the SamSam binary via the server to all connected hosts.
The ransomware then encrypted all PCs’ data and displayed the ransom note to the breached company, allowing the company to pay for each computer in part, or in bulk for all infected workstations.
“A relatively small percentage choose to only pay for individual machines,” a Sophos spokesperson told Bleeping Computer via email. “Most victims paid the full ransom amount sometimes after paying for an individual machine as a test first.”
SamSam crew becoming more cautious
Across time, Sophos says it identified at least three major SamSam ransomware versions, each receiving more and more protection measures to prevent security researchers from analyzing its inner-workings.
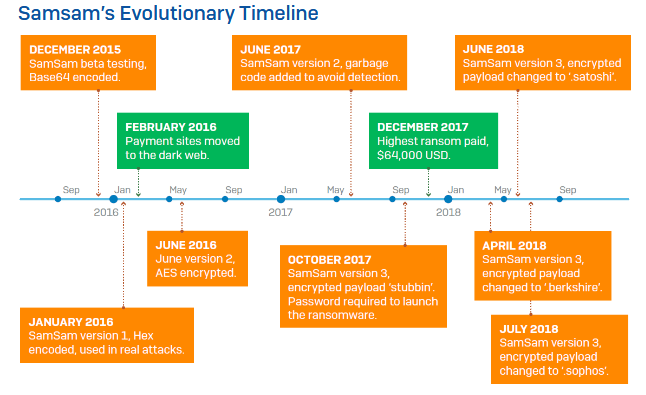
Sophos notes that as time went by, the SamSam operators became more and more cautious, moving the ransom payment sites to the Dark Web and deploying more obfuscation for the SamSam code.
The reason is that after almost three years of targeting companies across the world, law enforcement and security firms are desperate to find any clues that may lead them back to its creators.
But Sophos doesn’t believe SamSam is the work of a group. In its report, the cyber-security firm claims that based on language analysis of all the ransom notes and the ransom payment portal, in addition to various other behavioral quirks, the SamSam ransomware appears to be the work of a lone individual, rather than a group.


