Equinix Data Center Giant Hit by Netwalker Ransomware, $4.5M Ransom
Ransomware attackers are demanding $4.5 million from Equinox
read morePublished on: February 12th, 2018
By Catalin Cimpanu
February 12, 2018 01:20 PM 0
Cryptojacking script targeting Android devices
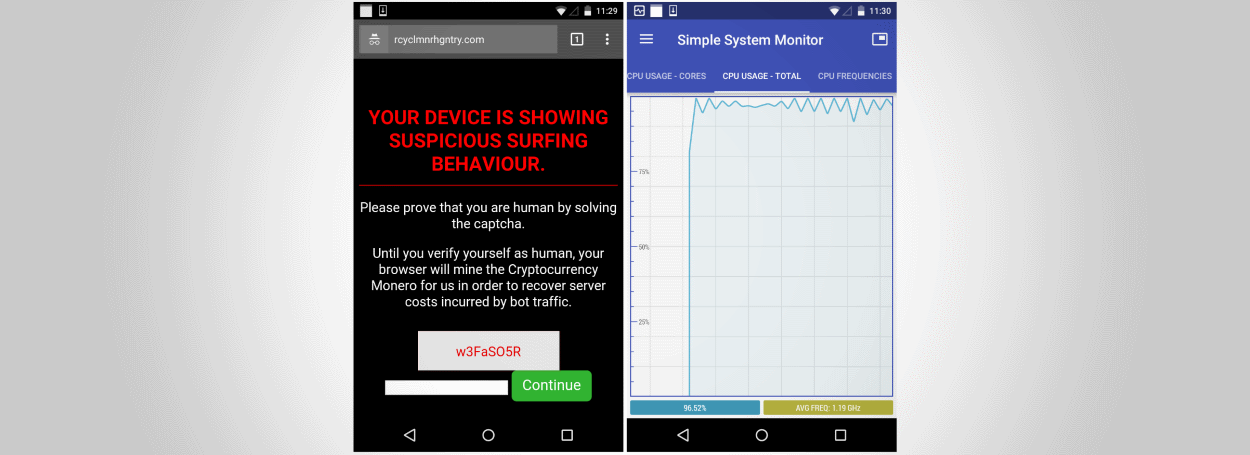
Threat actors behind a malvertising campaign are explicitly targeting mobile web users, redirecting Android owners to websites where crooks mine Monero using the Coinhive service while the user is busy solving a CAPTCHA.
Spotted by Malwarebytes, this campaign appears to have started in November last year. The modus operandi is simple. Crooks hijack traffic from legitimate sites using malicious ads and redirect users to other domains.
Desktop users get scamware; mobile users get cryptojacking
While desktop users are redirected to websites hosting tech support scams, mobile users are redirected to domains where they’re asked to solve a CAPTCHA to continue.
The trick is that during all the time the user is trying to solve the CAPTCHA using the smartphone’s clunky keyboard, the site loads and runs a cryptojacking script. This script utilizes all the phone’s CPU power to mine Monero.
Solving the CAPTCHA doesn’t do anything, as this just redirects users to the Google homepage. Crooks are only interested in keeping users on their site as long as possible while they mine Monero in the background.
Crooks making a few thousand dollars per month
Researchers have identified five domains used in this malvertising campaign, all hosting the same page and all with the same CAPTCHA code.
Malwarebytes says that based on traffic estimates, crooks attracted around 800,000 visits per day on all five domains, with an average time of four minutes spent on the mining page per user.
“It is difficult to determine how much Monero currency this operation is currently yielding without knowing how many other domains (and therefore total traffic) are out there,” said Jérôme Segura, Malwarebytes researchers. “Because of the low hash rate and the limited time spent mining, we estimate this scheme is probably only netting a few thousand dollars each month.”
The sum is inferior when compared to numbers associated with ransomware and crypto-mining malware. Nonetheless, in-browser crypto-mining attacks are on the rise because there is little pressure from law enforcement on this front, cryptojacking scripts don’t require advanced coding skills, and attacks can be scripted and automated, meaning less work for the threat actors.
Malwarebytes says that the lack of “web filtering or security applications on mobile devices,” is the reason why crooks developed and deployed this campaign in the first place. Android users should also be aware that mining crypto-coins on their smartphone may permanently damage the phone, hence, they should not take cryptojacking incidents lightly when they occur on their mobile devices.
With an evolving business comes expanding technological needs. If your business is sending you any of these signs that it’s time to update your technology.
Ransomware attackers are demanding $4.5 million from Equinox
read moreCybersecurity executives claim working from home increases the risk of attacks.
read more© 2024 Computer Troubleshooters. Privacy Policy