Equinix Data Center Giant Hit by Netwalker Ransomware, $4.5M Ransom
Ransomware attackers are demanding $4.5 million from Equinox
read morePublished on: May 31st, 2017
Posted: May 29, 2017 by Malwarebytes Labs
Last updated: May 30, 2017
Ransomware has become a popular criminal business with a relatively easy entrance. Even the people with little technical knowledge can build their own ransomware-based on open source code, that has been published on the internet some time ago. Nevertheless, cybercriminals keep stealing, not only from victims but also from each other. Some time ago we heard about PetrWrap – a ransomware built upon a binary of the infamous Petya. But that is not the only case. For some time, we have been observing a threat actor who distributes patched DMA Locker binaries.
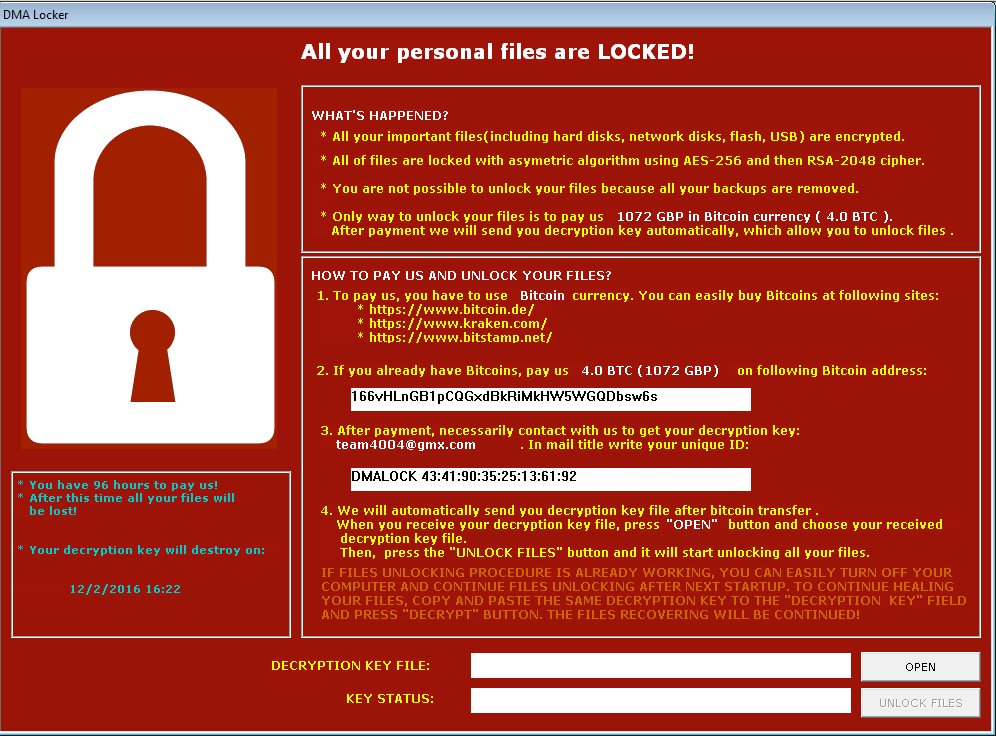
Real or stolen DMA Locker – why would you care?
The observed samples of the stolen version of DMA Locker have been built based on one and the same instance of DMA Locker – so, they carry inside the same public key. This implies, that all the victims of this version can get their data back with the help of the same private key. And now comes the best part: we have this key and we distribute it for free to all affected persons.
If you are a victim of the fake DMA Locker, you can send e-mail with samples of you encrypted files to: hasherezade-at-gmail.com
How to recognize the stolen versions?
Since the fake DMA Locker is based on the binary of the original DMA Locker 3.0, they have exactly the same GUI – only the keywords referring to DMA Locker has been removed:

The main difference between the original and stolen DMA Locker is a different marker at the beginning of the encrypted file. While the real DMA Locker prefixes content with: !DMALOCK, the stolen version have many different prefix patterns. Some we have observed are:
!XPTLOCK5.0
!Locked#2.0
!Locked!###
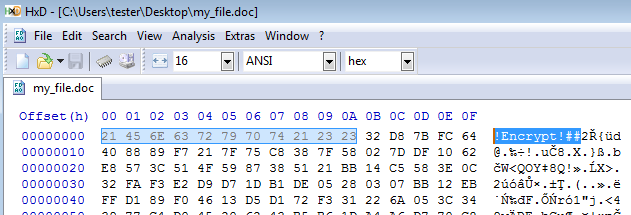
!Encrypt!##
However, the threat actor changes them periodically – so, anything that is different from the standard pattern may suggest that we are dealing with the “pirated”, decryptable version.
An example of the file encrypted by the fake DMA Locker:
What are the chances to get the data back?
Up to now, we managed to help 100% of the known victims of the fake DMA Locker. So far, the threat actor responsible for distributing it has not changed the key – so, the prospects of getting data back are still big. However, the chance to get help drastically shrink in case you were attacked with the legitimate DMA Locker, which may look the same at first sight.
How to prevent the attack?
Distributors of the fake (as well as the original) DMA Locker enter the victim machine via hacked Remote Desktop. Thus, we recommend paying attention if you have Remote Desktop open and if so, if it is properly secured.
Analyzed sample
https://hybrid-analysis.com/ – fake DMA Locker, adding “!Encrypt!##” prefix.
Appendix
Currently in distribution is version 3.0 of DMALocker, since the development of 4.0 was abandoned. Read more about our research:
With an evolving business comes expanding technological needs. If your business is sending you any of these signs that it’s time to update your technology.
Ransomware attackers are demanding $4.5 million from Equinox
read moreCybersecurity executives claim working from home increases the risk of attacks.
read more© 2024 Computer Troubleshooters. Privacy Policy