Equinix Data Center Giant Hit by Netwalker Ransomware, $4.5M Ransom
Ransomware attackers are demanding $4.5 million from Equinox
read morePublished on: August 28th, 2017
By Lawrence Abrams
August 28, 2017 04:01 PM 0
A new variant of the BTCWare ransomware was discovered by ID-Ransomware’s Michael Gillespie that appends the .[affiliate_email].nuclear extension to encrypted files. The BTCWare family of ransomware is distributed by the developers hacking into remote computers with weak passwords using Remote Desktop services. Once they are able to gain access to a computer, they will install the ransomware and encrypt the victim’s files.
Unfortunately, at this time there is no way to decrypt files encrypted by the Nuclear BTCware Ransomware variant for free. If you wish to discuss this ransomware or receive any support, you can use our dedicated Btcware Ransomware Support Topic. In the past, the developers have released the decryption keys for variants that were no longer in distribution. It appears they decided to no longer offer this to their victims. We hope they change their mind.
What’s New in the Nuclear Ransomware BTCWare Variant
While overall the encryption methods stay the same in this variant, there have been some differences. First and foremost, we have a new ransom note with a file name of HELP.hta. This ransom note contains instructions to contact [email protected] for payment information as shown below.
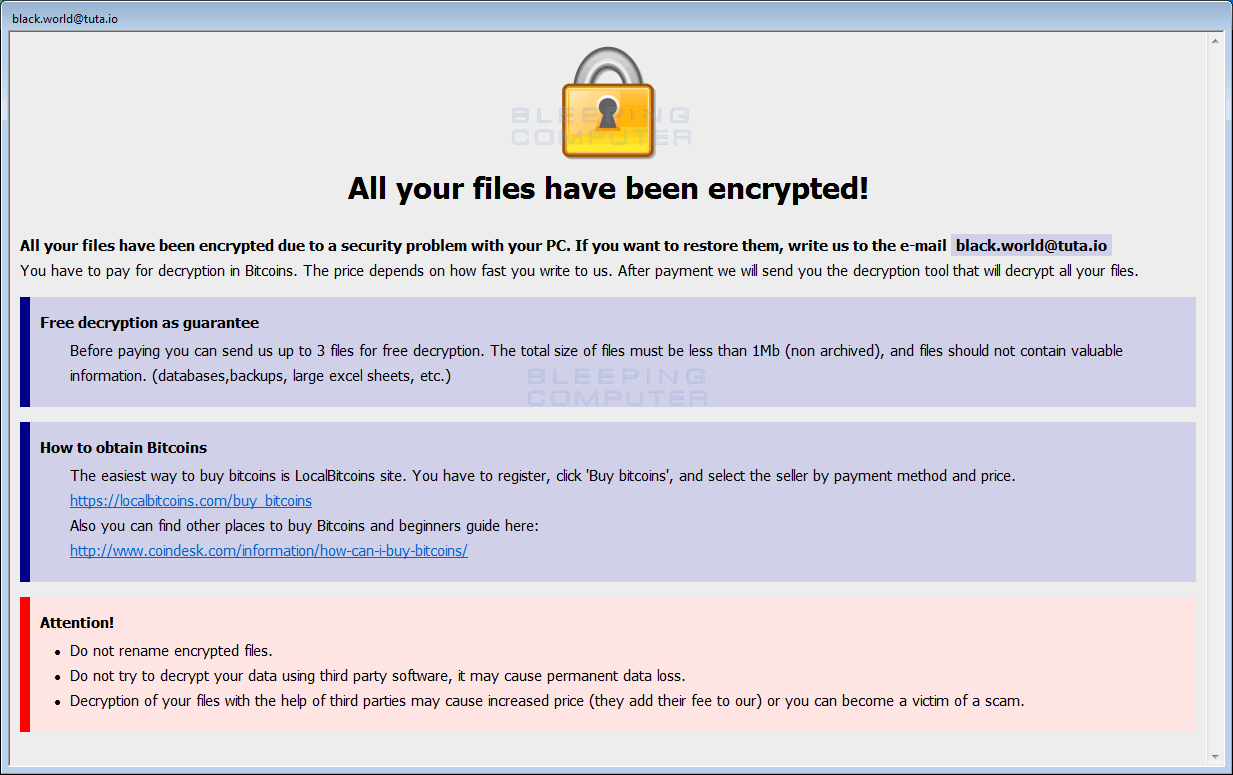
Nuclear Ransomware (BTCWare) Ransom Note
The next noticeable change is the extension appended to encrypted files. With this version, when a file is encrypted by the ransomware, it will modify the filename and then append the .[affiliate_email].nuclear extension to encrypted file’s name. For example, the current version will encrypt a file called test.jpg and rename it to test.jpg.[[email protected]].nuclear.
You can see an example of an encrypted folder below.
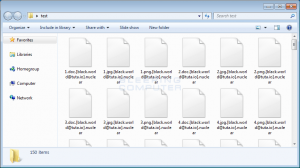
This variant also uses a different public RSA encryption key that is used to encrypt the victim’s AES encryption key. This public encryption key is:
—–BEGIN PUBLIC KEY—–
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDMwl0XpgillW5xCvuTbug+U+bVtZTaS0SRM+gNgaegG9PwsUXsxaqOLBg1zBxUxPcsJvUcQ/SKYWNsA49SIaMtSG2/b5rby2cnS8J4wwqkF0hDUFurF+t1o1TO6NDomgVMyak6nteJuR9ZAPUAmT3s4HqbhbL9Mh6h08iEl7jCbQIDAQAB
—–END PUBLIC KEY—–
If any new information or methods to decrypt the files becomes available, we will be sure to update this article.
IOCs
File Hashes:
SHA256: d5397a05b745f64ab16ff921fb4571e9072b54437080bc9630047465e6b06a41
Filenames associated with the Nuclear Ransomware Variant:
Help.hta
Nuclear BTCWare Ransomware Ransom Note Text:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail [email protected]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 3 files for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
With an evolving business comes expanding technological needs. If your business is sending you any of these signs that it’s time to update your technology.
Ransomware attackers are demanding $4.5 million from Equinox
read moreCybersecurity executives claim working from home increases the risk of attacks.
read more© 2024 Computer Troubleshooters. Privacy Policy