Equinix Data Center Giant Hit by Netwalker Ransomware, $4.5M Ransom
Ransomware attackers are demanding $4.5 million from Equinox
read morePublished on: June 18th, 2018
Nowadays, data breaches are a regular occurrence, affecting businesses and individuals across the world. Once your private data is in the hands of a hacker, your life and career can be turned upside down in a matter of minutes.
The problem is, most people don’t realize the importance of securing their online data, and this is especially the case when it comes to Google accounts. Your Google account includes not only email, but also your Google Drive documents and files, your photos, schedule of Google calendar, saved addresses on Google maps, and even your search history and search trends.
In fact, there is a lot more personal and professional data which can be accessed by anyone who hacks into your Google account.
By remaining ignorant about the importance of maximum account security, you could be making yourself vulnerable to a potential data breach even at this moment. Take a moment to go over the following simple steps and ensure that your Google account is as safe as possible from potential attacks.
First thing’s first: learn about your current account security and privacy settings here. Scroll down, and you’ll see two separate options; a Security Checkup and a Privacy Checkup.
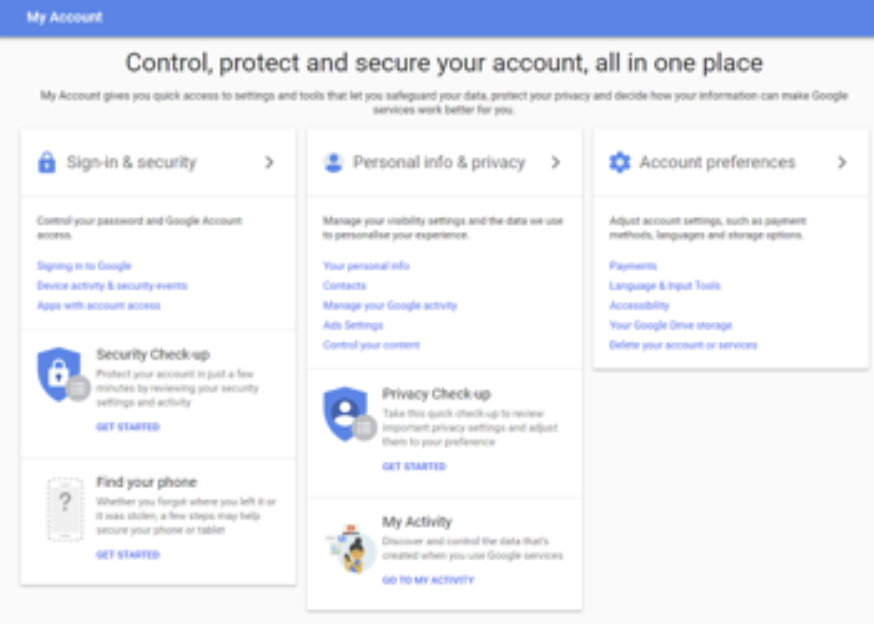
Click Security Checkup first and add your personal phone number to maximize security. By doing so, you will be informed by Google on text any time it detects unusual account activity such as a sign-in from an unfamiliar location or device. Make sure to manually check the alternate emails added to your account to ensure that they are all familiar.
Next click on Privacy Checkup to find out how much of your personal information is being shared with the world. Review the information shared on your Google+ profile, and see what information Google saves about you. You have the choice to enable or disable the different privacy options, and you can even stop Google from tracking your location.

If you haven’t already, you must set up 2-step verification immediately. Even if you have the most complex password in the world, it could even be revealed by an entrusted individual with the wrong intentions. 2-step verification enables Google to confirm that only the true account holder is demanding access.
Once you quickly set this feature up, a verification or confirmation code will be sent to your phone which must be inserted on a secondary log-in screen to access your account.

Under the Security Alerts section of account settings, browse through the devices which are connected with and have access to your Google account. Check the devices (computers, phones and tablets) which are logged into your account, and immediately remove the ones that you don’t recognize or don’t use anymore. It is wise to be overly cautious in this step, and remove all the devices which aren’t in regular use by you or someone you trust.
You should then look through the websites and applications which have permission to access your personal account information. Delete all the apps and sites you don’t trust or don’t use frequently.
Apart from these directions, it is also wise to set up an extremely complicated password (such as XjteQit!7452#kTPS) and frequently erase your search history and cookies. Remember to remain ever-cautious of your Google account security and check the settings at regular intervals for a couple of minutes to ensure that you are protected.
If you are concerned for the security of your valuable business data and information, CT Business Solutions Huntsville offers a range of IT services to guarantee supreme IT security.
Let CT Business Solutions Huntsville ensure that your valuable business data is protected, allowing you to direct your focus towards maximizing productivity.
With an evolving business comes expanding technological needs. If your business is sending you any of these signs that it’s time to update your technology.
Ransomware attackers are demanding $4.5 million from Equinox
read moreCybersecurity executives claim working from home increases the risk of attacks.
read more© 2024 Computer Troubleshooters. Privacy Policy