Equinix Data Center Giant Hit by Netwalker Ransomware, $4.5M Ransom
Ransomware attackers are demanding $4.5 million from Equinox
read morePublished on: April 20th, 2017
By Catalin Cimpanu
April 18, 2017 10:05 AM 0
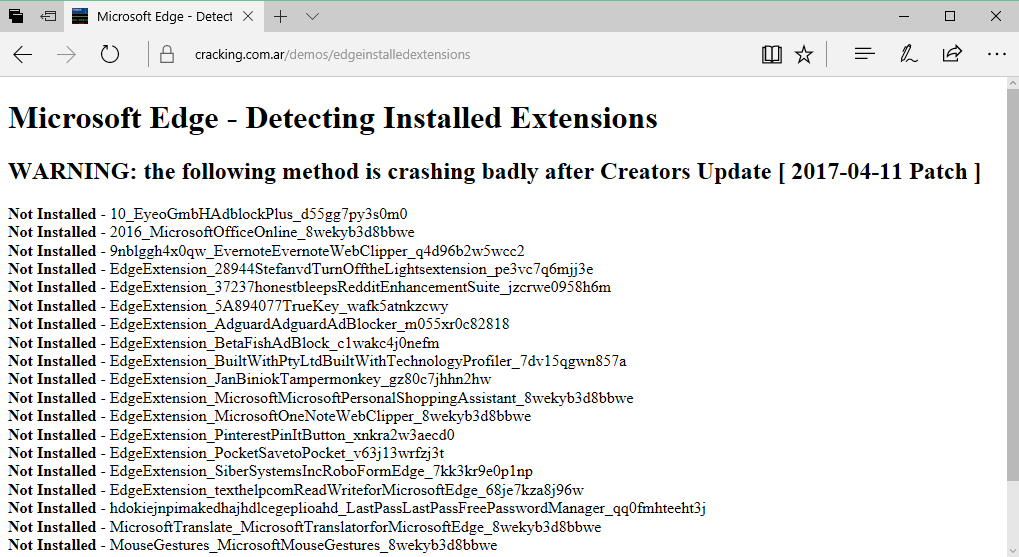
Microsoft never shied away from claiming that Edge is a much more secure browser than Chrome. Even some third-party tests have sustained its claims.
Nonetheless, there are currently three different issues affecting Edge, which Microsoft might not like you knowing about.
The first two were discovered by Argentinian security researcher Manuel Caballero, a man that has previously found other issues in Edge in the past.
Detecting a user’s Edge extensions
The first of these relates to user privacy, and more precisely to a flaw that a threat actor can exploit to detect a list of the user’s installed Edge extensions.
While knowing which Edge extension a user is using can be used to leverage vulnerabilities in that extension and hack a target, a more down-to-Earth scenario would be that advertisers could leverage that information to create more accurate user fingerprints, and use these fingerprints to track users across different sites.
The researcher said that the first method used to exploit this flaw was mitigated with the release of Windows 10 Creators Update, but he pointed out that there are two other ways this can still be exploited.
Using Edge’s new Reading Mode to bypass SOP filters
The second flaw Caballero discovered was in Edge’s “Reading View,” which is a browser feature that strips away all the ads and images and leaves only a page’s title and text, similar’s to Firefox’s Reader View.
The security researcher found a way to leverage to force a page to load into Reading View, even this isn’t possible for all URLs.
Because of a bug in Reading View, the attacker can load JavaScript code on this page that redirects the user to a new page, while the original URL remains in the address bar.
Caballero weaponized this bug by taking the URL from Google search results, which start with google.com but are actually redirects, to load that link in Reading View, but send users to malicious pages.
Second and third Reading View bugs the researcher discovered allowed him to load and execute code in this Reading View page, bypassing SOP (Same Origin Policy). The ability to execute code is dangerous, as the attacker could re-shape the page to look like the real Google login page but secretly record the user’s login credentials, all the time while showing google.com in the address bar.
This issue is not yet fixed. A demo page is here, and a YouTube video is available below.
With an evolving business comes expanding technological needs. If your business is sending you any of these signs that it’s time to update your technology.
Ransomware attackers are demanding $4.5 million from Equinox
read moreCybersecurity executives claim working from home increases the risk of attacks.
read more© 2025 Computer Troubleshooters.