Equinix Data Center Giant Hit by Netwalker Ransomware, $4.5M Ransom
Ransomware attackers are demanding $4.5 million from Equinox
read morePublished on: August 22nd, 2017

A new malware family detected under the name of CoinMiner is causing users and security firms alike loads of problems, being hard to stop or detect due to the combination of various unique features.
The malware — a cryptocurrency miner — uses the EternalBlue NSA exploit to infect victims and the WMI (Windows Management Instrumentation) toolkit as a method to run commands on infected systems.
In addition, CoinMiner also runs in memory (fileless malware), and uses multiple layers of command and control servers to deploy the multitude of scripts and components it needs to infect victims.
All of these make a deadly mixture of features that spell trouble for outdated machines and systems running antivirus solutions not up to par with the latest infection techniques.
Avoid getting infected with CoinMiner by disabling SMBv1…
To avoid getting infected with CoinMiner, there are a few precautionary measures that users need to take.
The simplest solution is to prevent the malware’s first infection step, which is EternalBlue, an SMB exploit developed by the NSA, leaked online by a hacker group known as The Shadow Brokers, and used in the WannaCry and NotPetya ransomware outbreaks.
Users should make sure they have the MS17-010 Microsoft security patch installed, or at least disable the SMBv1 protocol on their systems, so CoinMiner won’t have any way of reaching their computers.
… and WMI
In situations where this protocol is crucial for network interoperability, CoinMiner infections can still be avoided if users protect against the malware’s second exploitation stage, which is the usage of WMI — a set of tools built into all Windows versions.
CoinMiner uses WMI to download scripts and other components needed to get persistence on each host, and later to download and launch the actual CoinMiner binary.
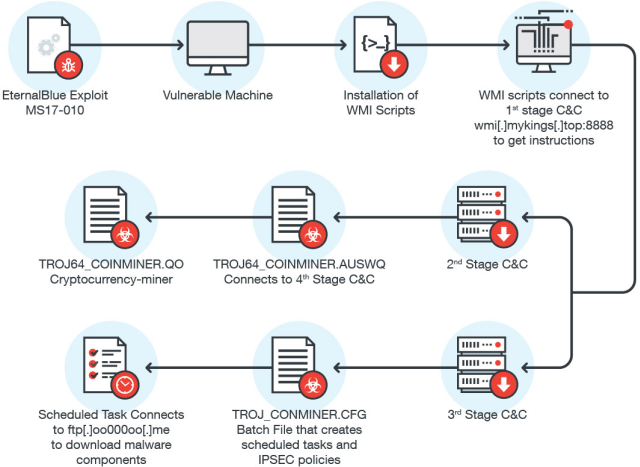
Trend Micro, the company that discovered CoinMiner this week, recommends disabling WMI on systems where it’s not needed, or at least restricting WMI access to only one admin account, accessible to IT staff only.
Guides for disabling both SMBv1 and WMI are available here and here. For the technically inclined, Trend Micro also published a technical report detailing the CoinMiner infection process step by step.
CoinMiner is not the first cryptocurrency miner to use the EternalBlue exploit to infect victims. The Adylkuzz miner was the first, deploying it shortly after The Shadow Brokers leaked it online. On the other hand, CoinMiner is one of the few fileless cryptocurrency miners around.
With an evolving business comes expanding technological needs. If your business is sending you any of these signs that it’s time to update your technology.
Ransomware attackers are demanding $4.5 million from Equinox
read moreCybersecurity executives claim working from home increases the risk of attacks.
read more© 2024 Computer Troubleshooters. Privacy Policy