Equinix Data Center Giant Hit by Netwalker Ransomware, $4.5M Ransom
Ransomware attackers are demanding $4.5 million from Equinox
read morePublished on: January 09th, 2017
By Catalin Cimpanu
January 9, 2017 06:11 AM 0
Despite the ever-evolving complexity of cyber-attacks and malware code, phishing and spear-phishing attacks remain the initial entry point in many of today’s security breaches.
In most phishing attacks, crooks leverage a common theme, asking users to update their profile information on various profiles, but redirecting users to pages hosted on lookalike domains.
As users have got accustomed to this basic phishing trick in recent years, attackers found other creative ways of phishing for login credentials.
One trick, first seen in June 2016, was observed again this past month. This clever phishing attack relies on telling users they received an important or secure file, and they need to visit a web page to view it.
The real trick takes place on the crook’s page, which shows a blurred out document on the background. To view the document, users have to enter their credentials.
The blurred out document seen in the page’s background acts as a promise for what users are going to receive if they authenticate. In fact, these are nothing more than simple web pages showing an image of a blurred out document, and nothing more. The only thing working on the page is the login form that will record any login credentials that you enter inside it.
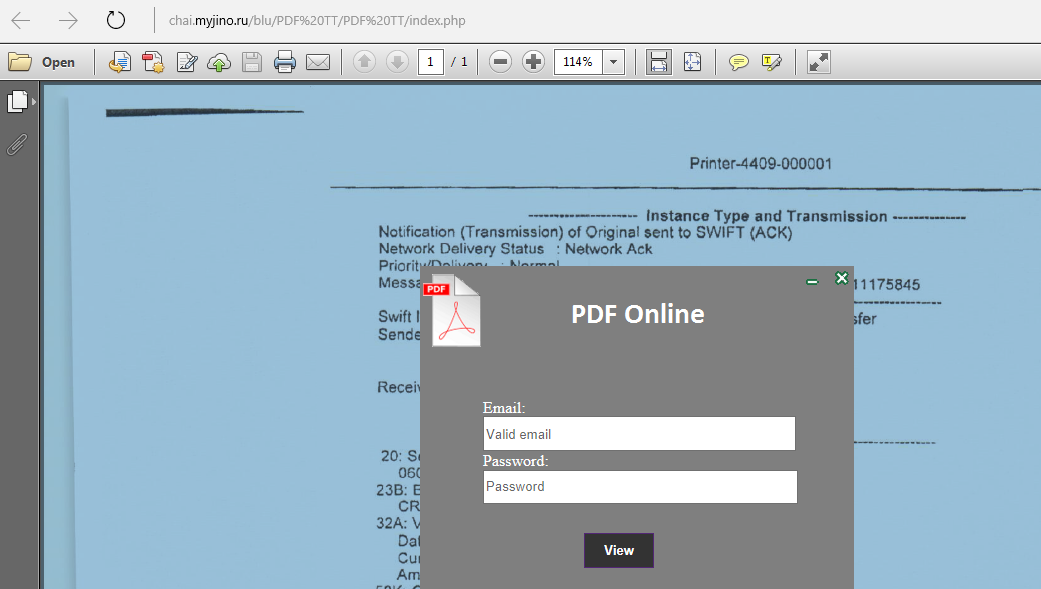
Just like the 2016 attacks, crooks don’t specify which login credentials users have to fill in, and leave it to the user enter what he thinks he should entered. A careless user could enter anything from his Intranet details to Google logins.
Right now, based on the 2016 and 2017 incidents, these attacks are quite easy to detect. If the crooks behind these phishing pages would be less sloppy and spend more time in refining details, these type of attacks could be quite effective and harder to detect for what they really are.
Below are some screenshots from the June 2016 campaign.
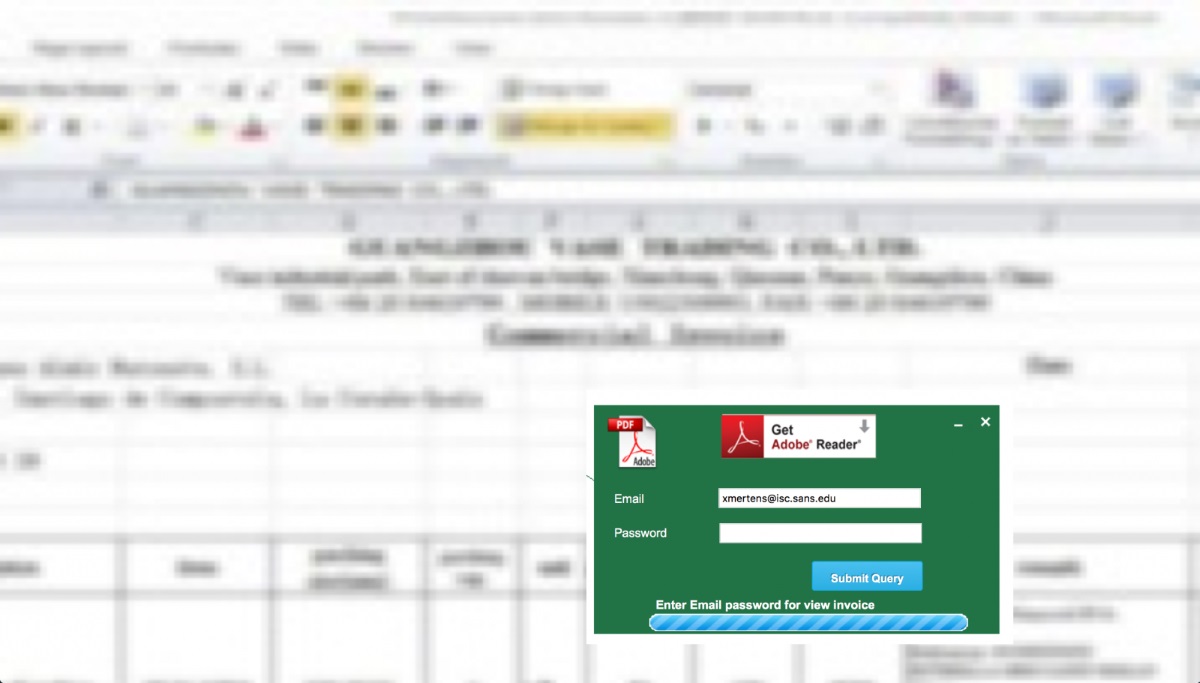
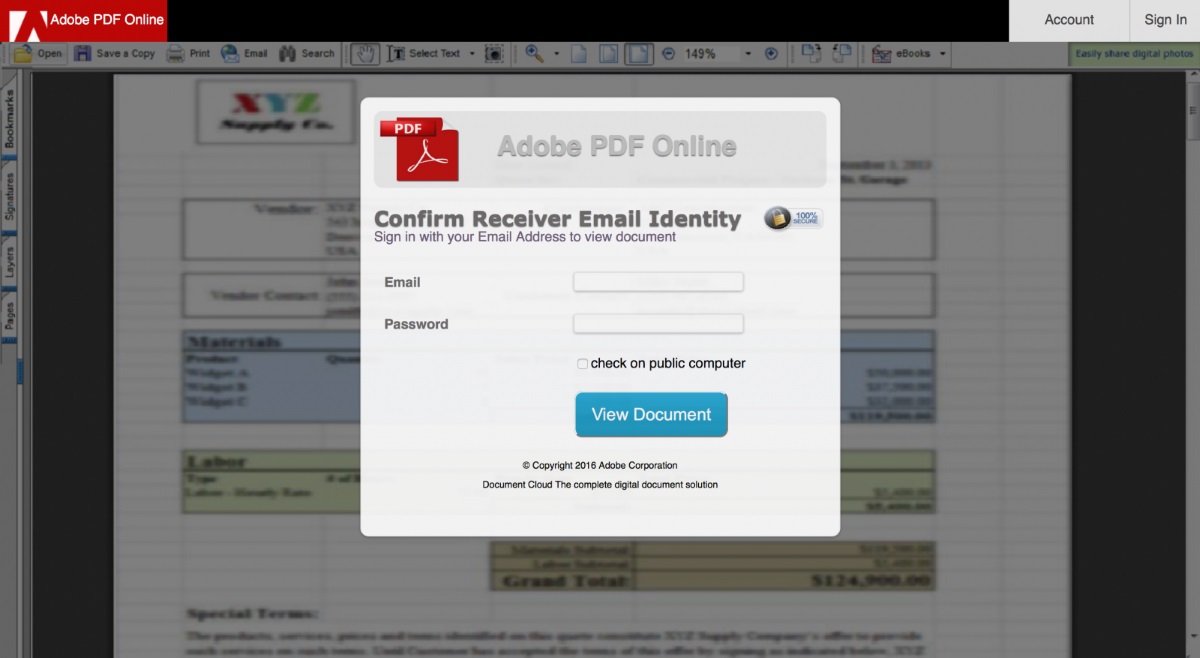
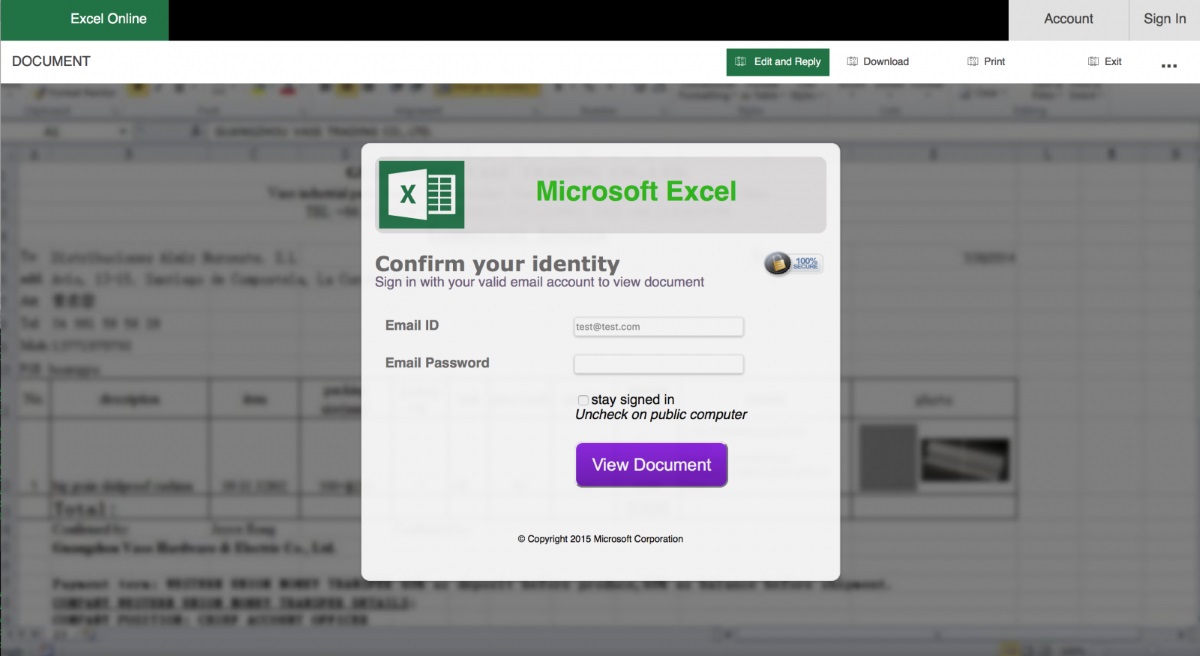
With an evolving business comes expanding technological needs. If your business is sending you any of these signs that it’s time to update your technology.
Ransomware attackers are demanding $4.5 million from Equinox
read moreCybersecurity executives claim working from home increases the risk of attacks.
read more© 2024 Computer Troubleshooters. Privacy Policy